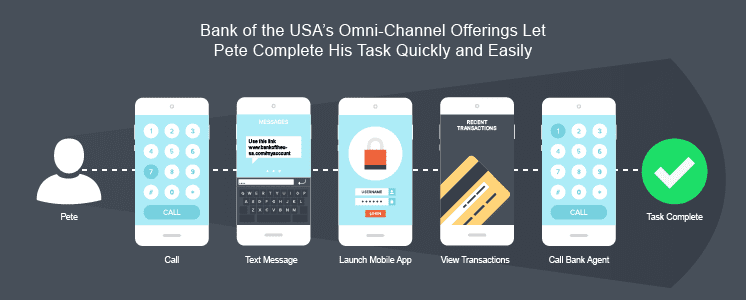
Just Say No to Resets: Seamless Customer Experience in Omni-Channel Communications
Omni-channel communications appeal to a lot of companies. And it makes sense that they do. Having that type of power at your disposal allows businesses to meet customers on their turf. While this means there are more channels to manage, when done right, the benefit is that omni-channel communications create a better customer experience. Omni-Channel …
Just Say No to Resets: Seamless Customer Experience in Omni-Channel Communications Read More »